
Get full visibility into your SaaS supply chain—shadow apps, risky OAuth grants, third-party integrations, unvetted vendors—so you can catch the hidden threats the rest of your tools miss.
Only Nudge Security can map your entire SaaS and AI supply chain—today.
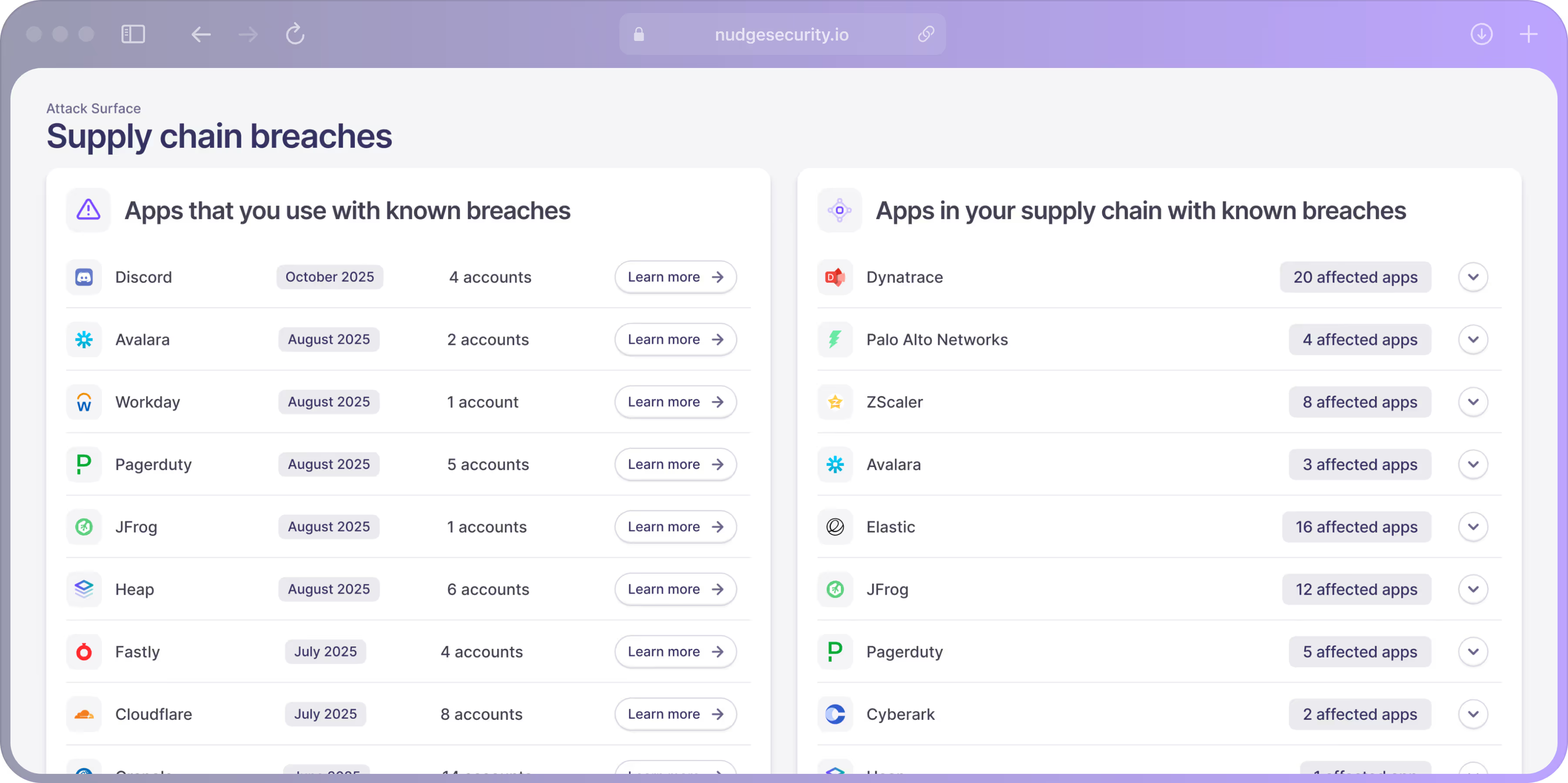
Breaches like Salesloft-Drift prove attackers don’t need to target your core systems directly. They can exploit the hidden web of SaaS apps, OAuth grants, and third-party dependencies—blind spots your traditional security tools will never see.
Instantly map your full SaaS supply chain, uncovering every app, integration, and vendor dependency.




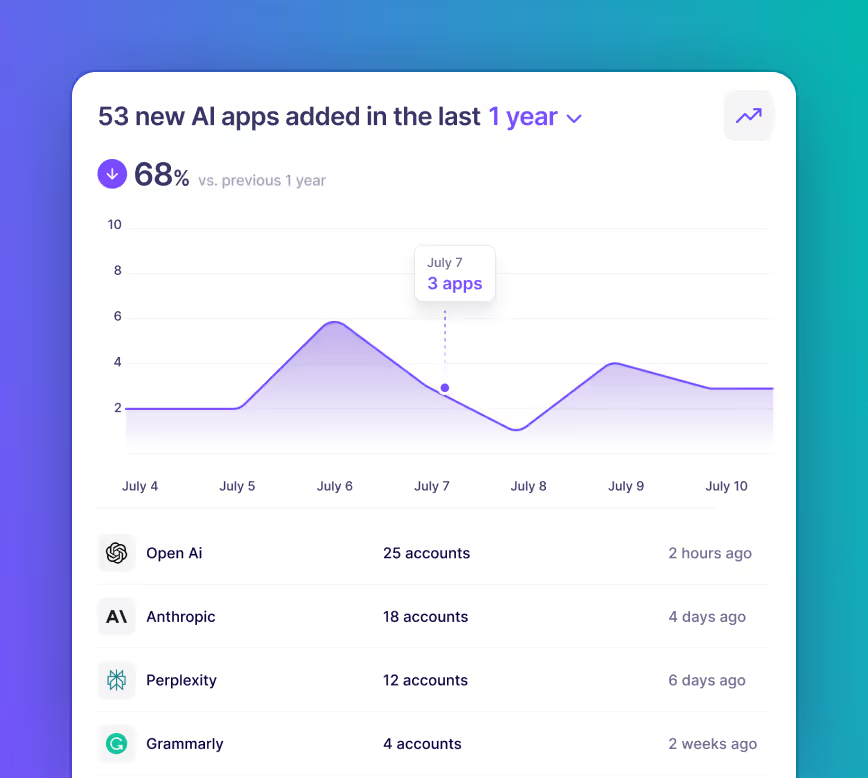

Quickly evaluate the security posture of every vendor and integration, with security profiles and risk insights for 175k+ SaaS and AI providers.




Continuously monitor for anomalies, permission changes, or potential breaches across your supply chain.




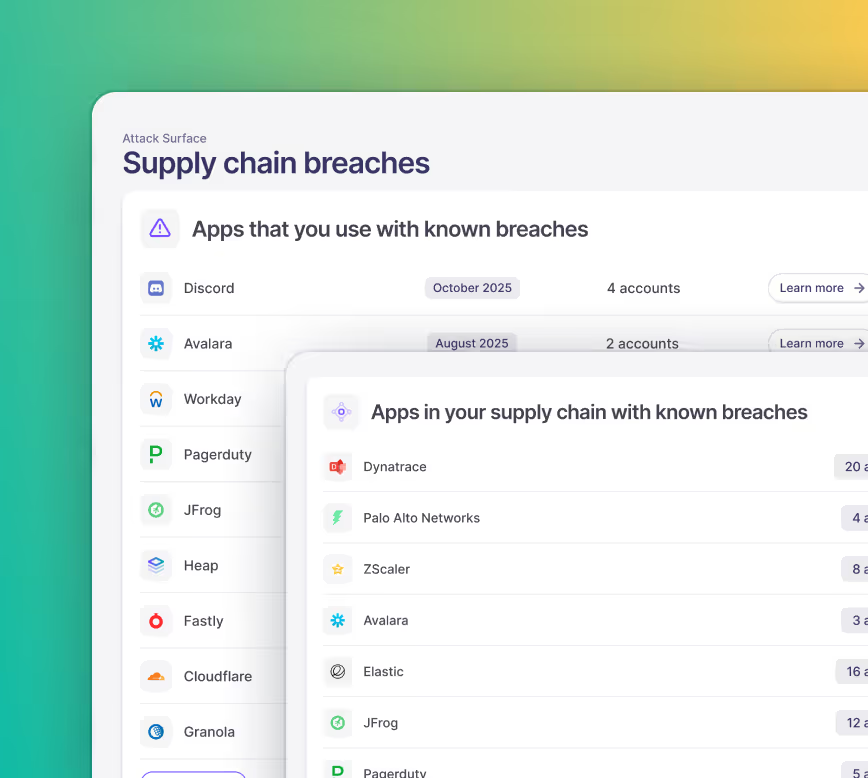
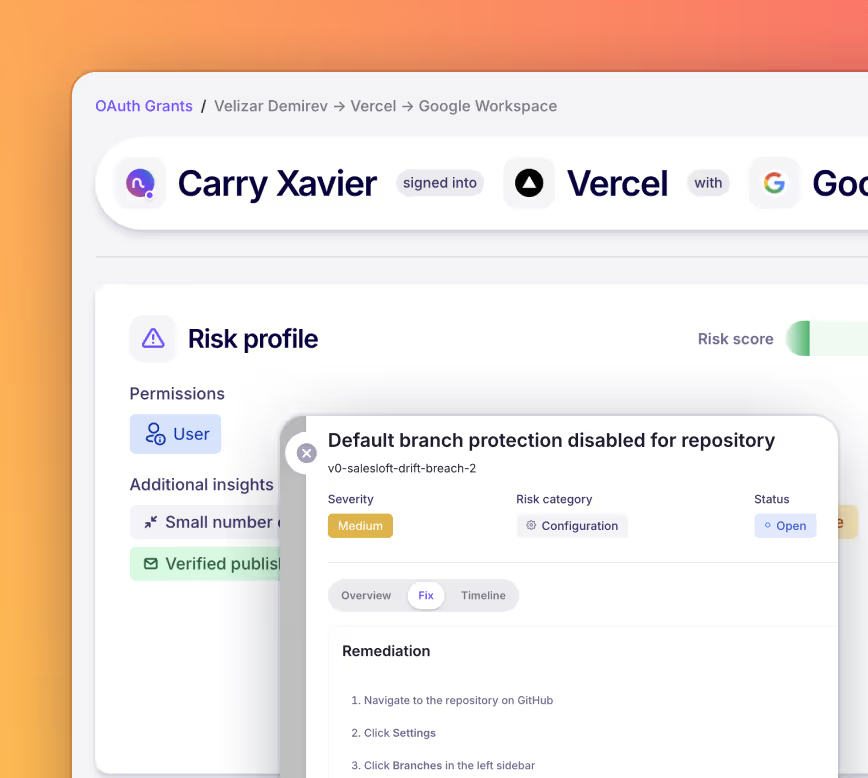
Reduce risk proactively by enforcing policies and remediating threats automatically.






Blind spots: unsanctioned apps, shadow vendors, unknown OAuth permissions
Long vendor reviews, sporadic audits, manual detection
Permissions drift, stale or excessive access left unchecked
Compliance & risk posture unclear; slow response to breaches

Full visibility: known & unknown apps, integrations, vendor dependencies
Continuous, automated risk detection, instant alerts, workflow driven
Least-privilege enforced, unused permissions revoked, identity drift controlled
Auditable, proactive posture management; breach detection; rapid remediation
Common questions about Nudge Security's SaaS supply chain security solution
SaaS supply chain security refers to protecting an organization from the risks and vulnerabilities that arise from its use of third-party SaaS vendors, and the vendors that those vendors rely on (i.e. 3rd-, 4th-, or even further parties). This includes understanding vendor security programs, breach histories, third-party dependencies, permission grants (OAuth etc.), integrations, and the potential blast radius if one vendor in the chain is compromised.
Several trends are accelerating risk: rapid proliferation of SaaS tools, many adopted without oversight (shadow SaaS); increasing dependency on inter-vendor integrations and cloud services; SaaS providers themselves outsourcing services or depending on other SaaS providers; increased supply chain attacks in headlines; and regulatory/industry pressures for transparency. Collectively, these mean that an organization can be impacted by breaches or misconfigurations not just at vendors it directly contracts with, but upstream in that vendor’s supply chain.
Most organizations can deploy Nudge Security in under an hour. Our platform integrates with your existing identity providers (Microsoft 365, Google Workspace, Okta, Azure AD) and doesn't require any endpoint agents or network proxies. You'll start receiving insights about AI tool usage immediately after deployment, allowing you to take action from Day One.
Nudge Security provides automated discovery and continuous mapping of your SaaS supply chain including downstream and upstream dependencies. It surfaces vendor security reviews, breach history, risk & compliance data for both direct vendors and their own vendor dependencies (4th parties). It also reveals permissions via OAuth, shows how apps are connected (which employees granted what access), and categorizes vendors to help filter by type and risk.
You receive real-time breach alerts when a vendor (or a vendor’s vendor) is subject to a data breach that could affect your organization. The platform includes detailed breach history for your SaaS providers, so you can assess which apps might be in the blast radius. It also helps you understand the scope of impact, so you can respond swiftly and appropriately.
Nudge identifies several kinds of risk: overly permissive OAuth grants; invisible integrations or chain dependencies (third- or fourth-party services) with weak or unknown security practices; vendor misconfigurations or gaps in compliance programs; lack of credential hygiene or identity risk; permissions and access paths that allow for lateral movement; and insufficient visibility over what upstream dependencies a vendor relies on.
Traditional vendor risk assessments are often manual, one-off, or time-delayed; they may only cover direct vendors and skip vendor dependencies (4th parties), miss dynamic connectivity, or lack real-time breach feed or alerting. Nudge automates much of the mapping of supply chain (including upstream dependencies), OAuth permissions, breach alerts, and continuously monitors vendor risk posture. It also allows integrating these insights into workflows and automations, so risk isn’t just observed but remediated.
Very quickly. After deployment, you’ll see your SaaS inventory and vendor dependency mapping populate within minutes. OAuth permissions, vendor/breach-history data, and risk/capability assessments begin showing up shortly thereafter. Many organizations spot high-risk vendor dependencies or risky permissions within days, enabling early remediation.
Nudge aims to provide high fidelity visibility via multiple data sources: vendor metadata, breach history, OAuth and identity/permission data, direct vendor security and compliance program information. That said, gaps can exist: some vendors may not publish complete security data; some dependencies may be proprietary or opaque; some breach disclosure delays may affect timeliness; some integrations or vendor-vendor linkages might be hidden or not detectable by public or accessible metadata. Nudge surfaces confidence and gaps so security teams can prioritize remediation where risk is highest.
Knowing your full supply chain and vendor risk landscape makes audit response faster, supports compliance with regulations requiring vendor due diligence and breach disclosures, helps maintain a documented inventory of SaaS vendors and their upstream dependencies, enables policies and controls over OAuth access, allows continuous monitoring, and automates parts of risk management workflows. For audit or regulatory requests, being able to point to vendor breach histories, supply chain maps, and real-time alerting adds credibility and reduces manual effort.
Best practices include maintaining continuous discovery and mapping of SaaS vendors and their dependencies; enforcing least-privilege permissions and auditing OAuth grants; monitoring vendor breach history; using automated alerts; integrating supply chain risk into procurement and vendor onboarding; and empowering employees with visibility and nudges for secure behavior (e.g. limiting risky permissions, avoiding unmanaged vendors). Nudge enables these by automating discovery, supplying vendor profiles and breach data, providing security-focused dashboards, enabling permission visibility, and offering remediation workflows and automation so you can operationalize best practices rather than just observe them.
